Secrets Management
Secrets let you store encrypted credentials (API keys, cloud-provider keys, Databricks tokens, etc.) so that notebooks, jobs, and connectors can authenticate without exposing sensitive values in plain text.
Scope Levels
| Scope | Visibility |
|---|---|
| User | Only the creator can read/use |
| Workspace | All users in one workspace |
| Tenant | Visible to all users within the tenant |
Precedence: If a secret with the same name exists at multiple levels, the most specific one wins (
User → Workspace → Tenant).
Secrets Dashboard
Navigate to Secrets in the left sidebar.
Tabs across the top let you switch between User / Workspace / Tenant scopes.
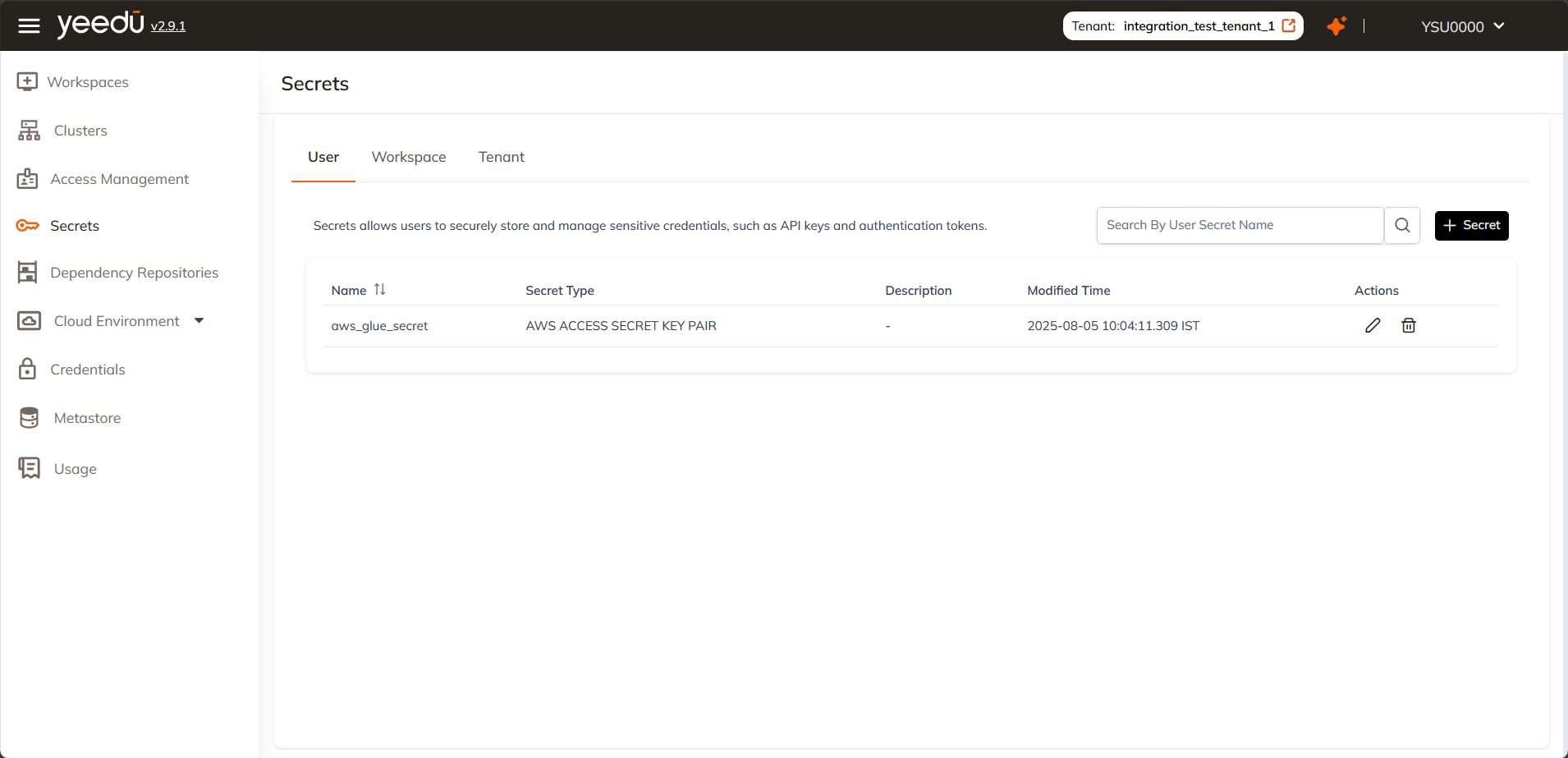
The Secrets dashboard lists all the secrets along with key information. Here's what each column means:
- Name: This is the identifier for the secret. It must be in lowercase, can be up to 64 characters long, and may include the characters
-,_,@, and. - Secret Type: Indicates the type of credential stored. This could be an environment variable, an AWS access key, a Databricks token, and so on.
- Description: An optional note that helps explain the purpose of the secret. This is useful for other users or for auditing later.
- Modified Time: Shows when the secret was last updated.
- Actions: Lists the actions you can perform on the secret:
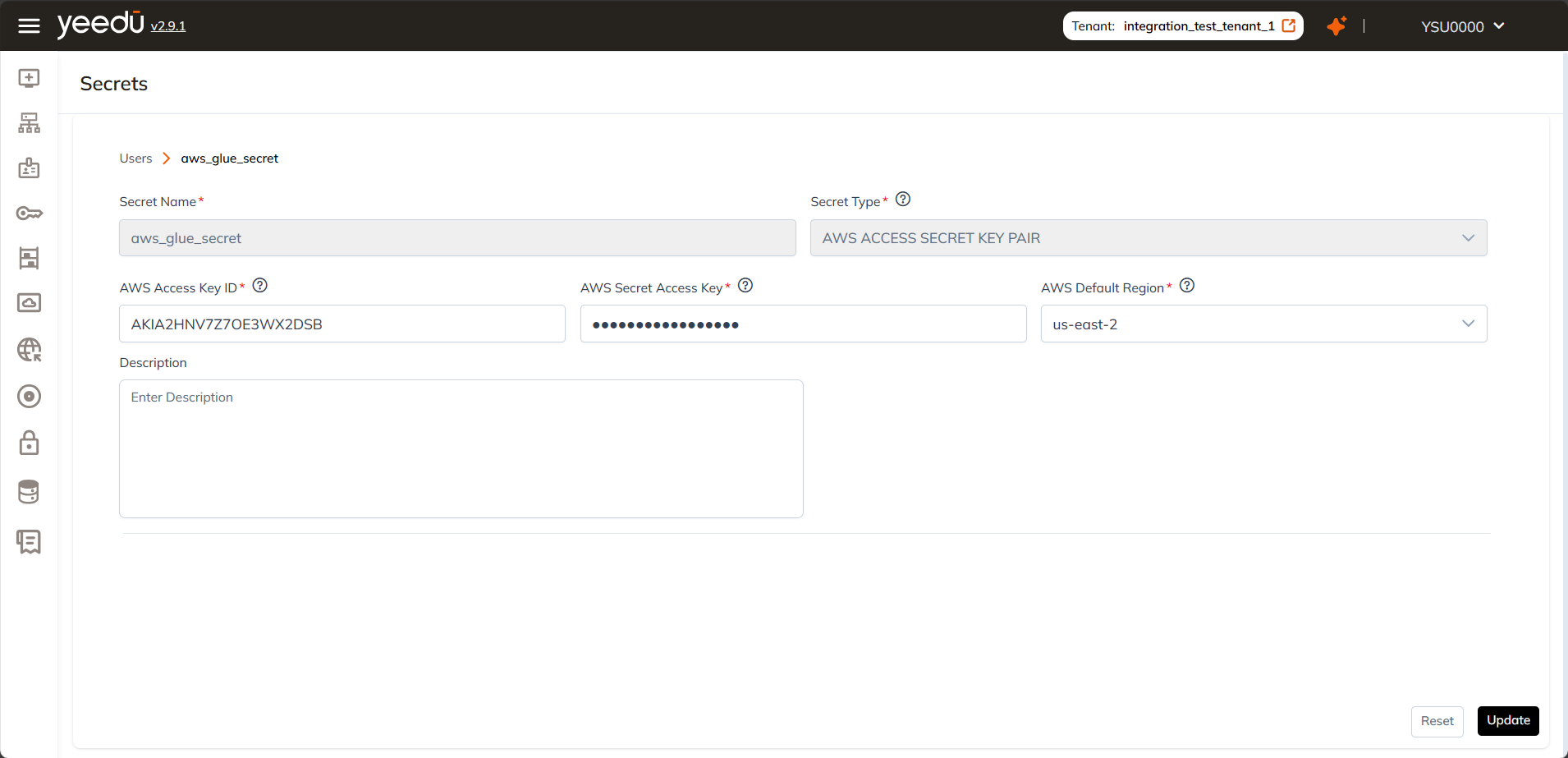
- Edit: Modify the name, value, or description of the secret.
- Delete: Permanently remove the secret from the system.
Creating a Secret
- Select the desired tab (User, Workspace, or Tenant).
- Click
+ Secret. - Fill out the form:
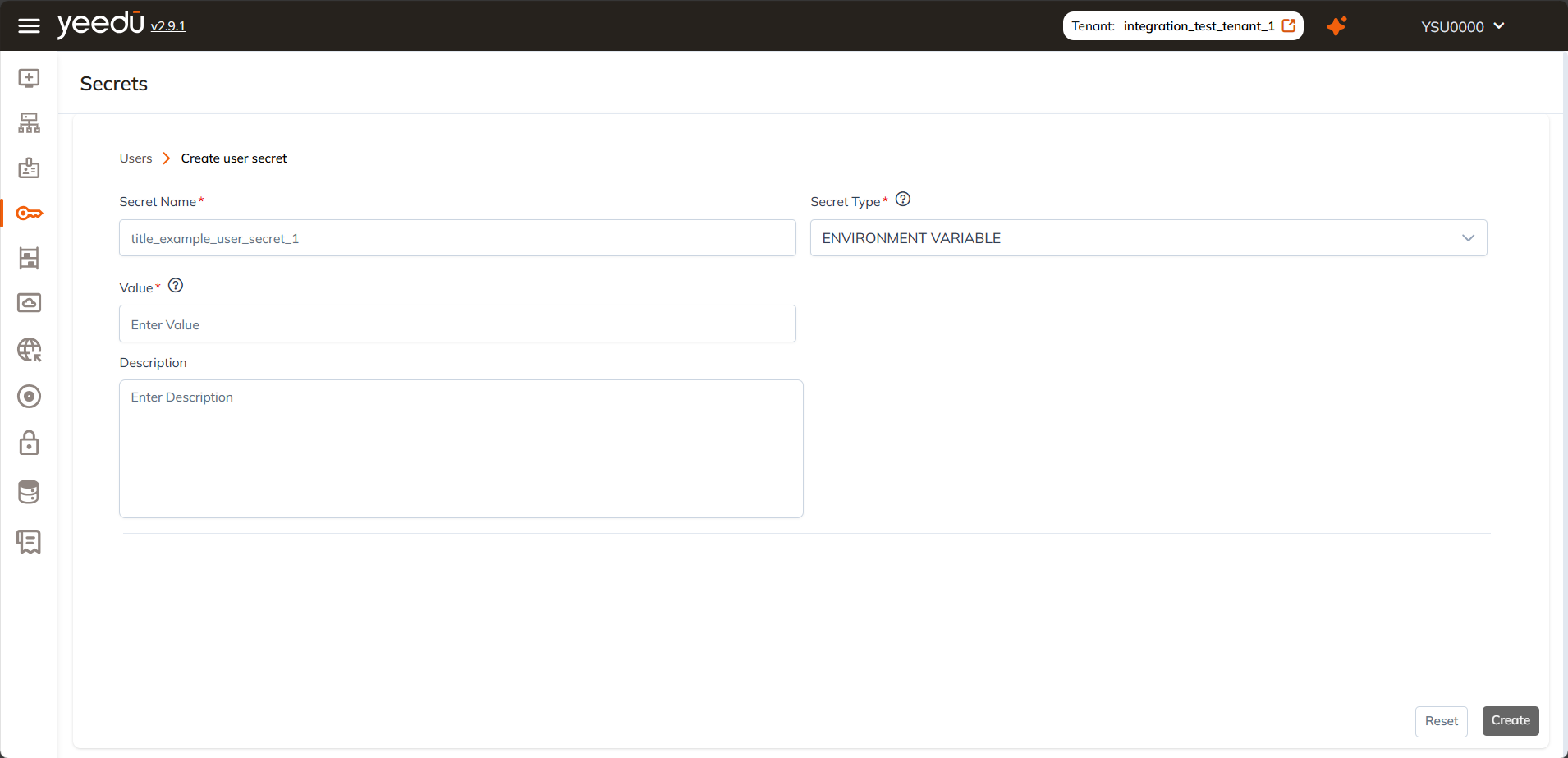
Secret Creation Fields
When creating a new secret, you'll be asked to provide the following details:
- Secret Name: The unique name of the secret. It must follow the defined naming rules (e.g., lowercase letters, max 64 characters, allowed symbols:
-,_,@,.). - Secret Type: Select the type of secret from the dropdown menu. Supported types include environment variables, cloud credentials, Databricks tokens, etc.
- Value: Enter the actual credential (token or key). This value will be masked and not viewable after creation, so make sure to store it securely.
- Description: (Optional) Add a short note to describe the secret’s purpose. This helps teammates understand its context and usage.
- Click
Create. The value is now encrypted at rest and never displayed again.
Supported Secret Types
- Environment Variable
- Databricks Unity Token
- Google Service Account
- AWS Access Secret Key Pair
- Azure Service Principal
- Hive Basic
- Hive Kerberos
Managing Secrets
| Action | Effect |
|---|---|
| Edit | Change value, description, or type |
| Delete | Permanently remove |
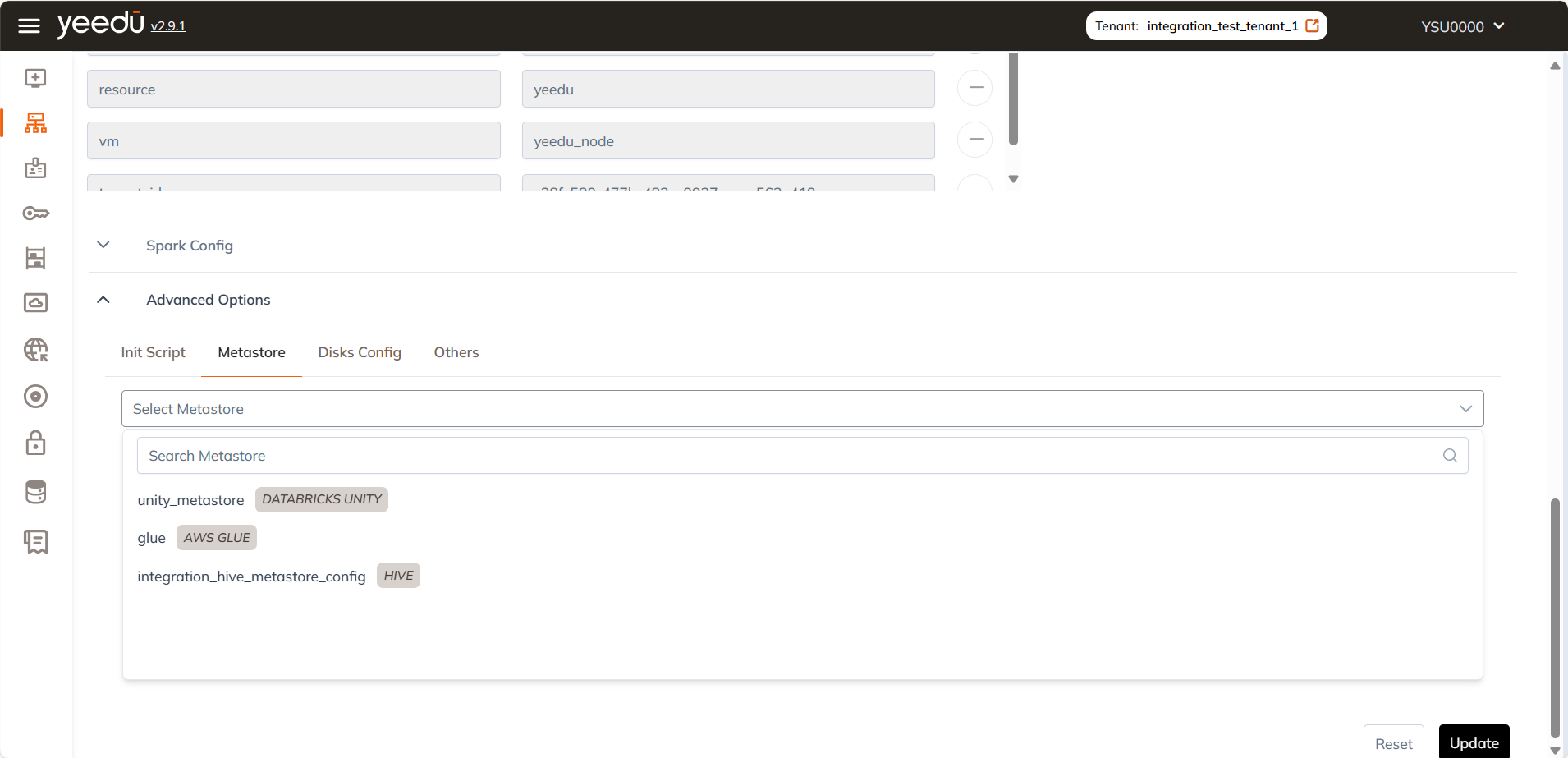
Using Secrets in Unity Catalog / Jobs
| Purpose | Secret Type |
|---|---|
| Databricks API auth | Databricks Unity Token |
| Cloud storage layer | AWS Access…, Azure Service Principal, Google Service Account |
| Spark Jobs | Environment Variable |
Attach these secrets to your Metastore or jobs via the Access or Dependencies tabs.
Security Best Practices
- Granular scopes: Personal tokens → User; shared creds → Workspace; infra-wide creds → Tenant
- Describe every secret for easy auditability.
- Review & purge unused or disabled secrets on a schedule.
The recommended resolution for Yeedu UI is 1920 x 1080.